Introducing MalChain : A Malware Kill Chain Framework
MALWARE ANALYSIS
f0xypr0xy
11/23/20251 min read
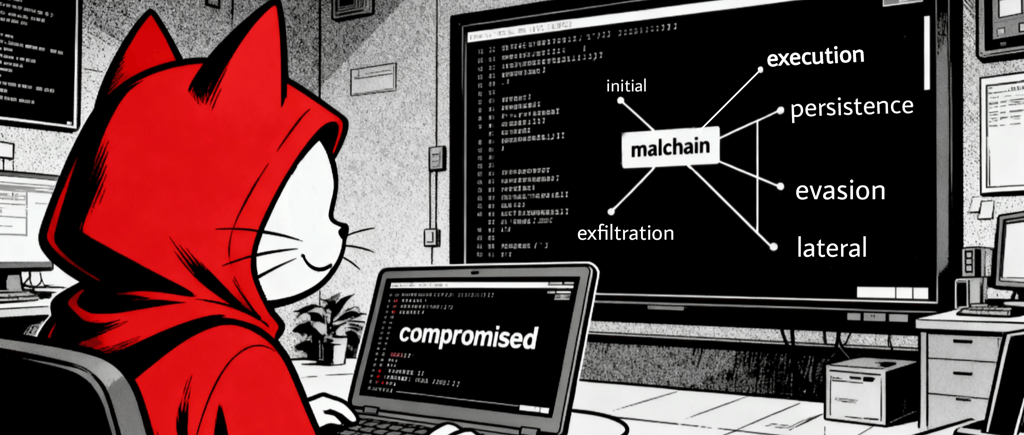
MalChain
An open-source framework designed to map malware behavior across six distinct attack phases, from initial access through data exfiltration. It bridges the gap between malware analysis and threat hunting by providing a structured way to understand adversary tactics at each stage of the attack lifecycle.
How MalChain Works
This framework helps in identifying the methods used by attackers at each phase of the attack lifecycle.
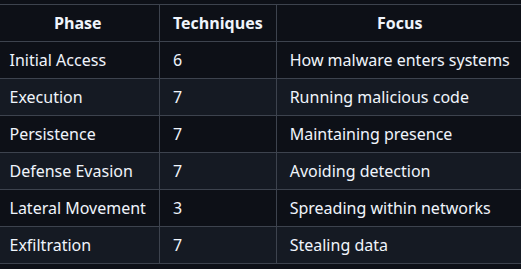
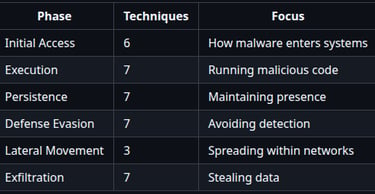
Each phase maps to specific techniques with detection methods and real-world examples.
Refer the complete framework table at :
https://github.com/Malwarehunts/Malchain/blob/main/docs/FRAMEWORK.md
Framework overview
Malchain visually maps malware behavior according to associated tactics and techniques. In this structure, tactics form the columns, each representing the adversary’s objective at a specific stage of the intrusion.
Tactic-Based Detection
The core idea : A malware variant you've never seen before might use a novel packing technique, but it still needs to achieve the same objectives as every other malware. By understanding these objectives, you detect the attack regardless of the specific implementation.
Modern malware easily slips past traditional tools like threat-intel feeds and routine monitoring. These samples are built to avoid signatures through polymorphism, encryption, and fileless execution.
A better approach is tactic-based detection. Instead of chasing indicators, it focuses on what the attacker is trying to do at each stage of the kill chain. By mapping detections to tactics and techniques, teams can spot the behavior behind the malware, not just its artifacts.
This strengthens early detection of advanced threats and improves threat-hunting overall. Even when signatures fail, analysts can still catch subtle behavioral clues and respond before the attack causes real damage.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.