The MMIO_Stale_Data Vulnerability
VULNERABILITIES
Cipherc4t
10/5/20252 min read
MMIO_Stale_Data is a class of CPU side-channel vulnerabilities, primarily affecting Intel hardware.
Intel disclosed these flaws in 2022 under the name “MMIO Stale Data Vulnerabilities” (CVE-2022-21123, CVE-2022-21125, CVE-2022-21127, CVE-2022-21166).
The problem
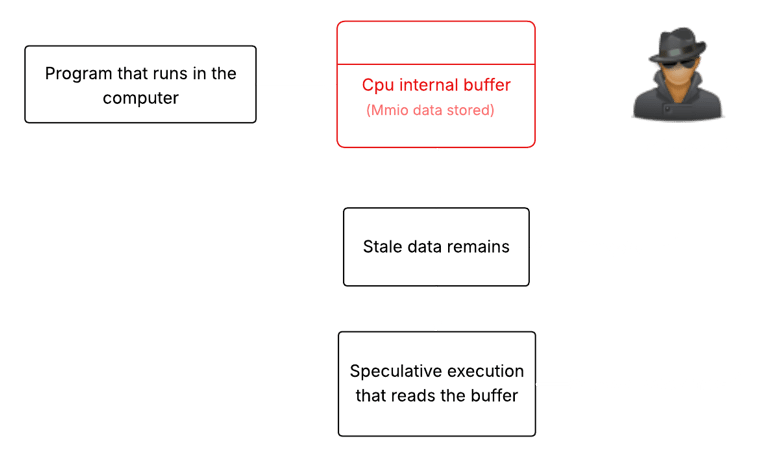
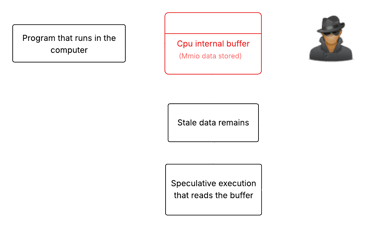
When certain instructions interact with memory-mapped I/O (MMIO) registers ,the leftover stale data from previous operations can be speculatively exposed to unprivileged code. This may lead to data leakage across security boundaries.
For example, from a guest VM to the host in a virtualized environment.
How the Vulnerability Works
Your Intel CPU has small on-chip storage areas called buffers that temporarily hold data while the CPU moves information. With the MMIO stale data vulnerability, old data can remain in these buffers longer than intended.
An attacker can trick the CPU into exposing that leftover data via speculative execution (when the CPU guesses instructions ahead of time). If successful, the attacker can read sensitive values from another program, the OS, or a guest VM.
For most desktop users, the risk is low once the system is patched. MMIO stale data cannot be exploited via phishing, downloaded malware, or typical remote attacks. It is a local micro architectural side-channel, meaning an attacker needs code running on the same physical core (or a sibling hyper thread) to observe the leftover data.
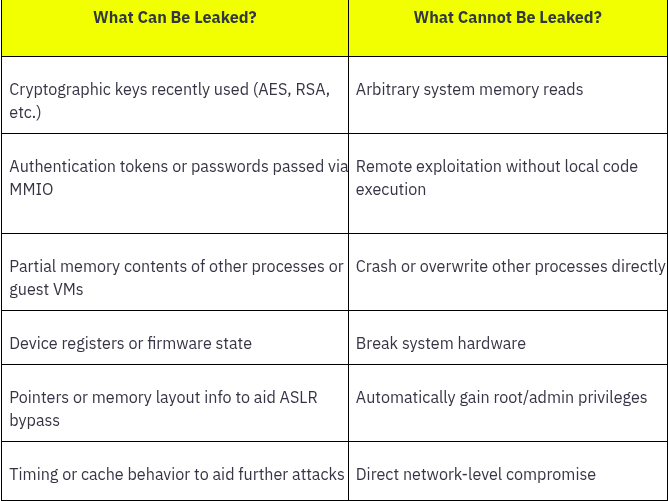
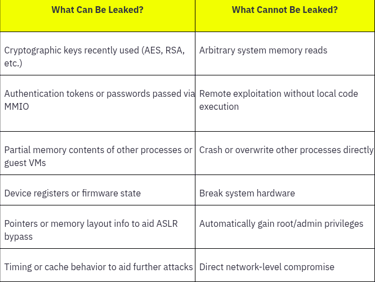
Mitigation : Intel provided microcode updates with OS-level mitigations.
Vulnerable CPU generations
Intel’s MMIO Stale Data vulnerability affects all processors up to the 11th generation. These CPUs require microcode and OS updates to reduce risk, but the flaw remains in the hardware. Starting with the 12th generation (Alder Lake), Intel redesigned the CPUs, fixing the issue in hardware, so no additional patches are needed.
Linux mitigates the risk by clearing CPU buffers, but if Hyper-Threading (SMT) is enabled, a small chance of data leakage remains.
For typical use, this is generally safe, but the only way to completely block it is to disable Hyper-Threading in the BIOS, which may reduce system performance.
Recommendations
Update the CPU microcode (Intel) and apply the latest kernel patches .
If you host untrusted VMs, containers, or multi-tenant workloads, consider disabling SMT on the host.
For maximum performance, keep SMT enabled but ensure microcode and OS mitigations are applied. For strict isolation, disable SMT.
To learn more about SMT-related risks and the security impact of disabling Hyper-Threading (SMT), refer to the blog below.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.

