Using Python Virtual Environments for Safe Malware Analysis
LINUX
Cipherc4t
10/18/20253 min read
When installing malware analysis tools like Volatility or YARA on Linux, you may run into version conflicts or dependency errors. For example:
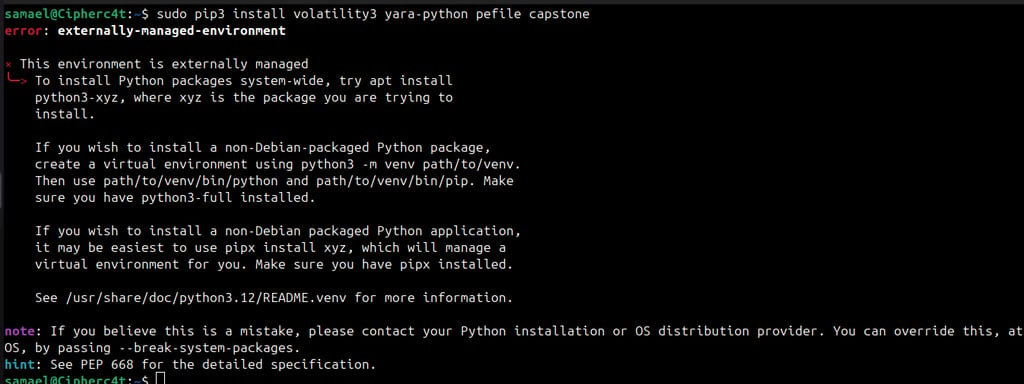
The “external-managed-environment” error appears when you try to install Python packages system-wide for your analysis tools.
Reason
System tools that use the distro’s Python or Python libraries can break if your analysis tools overwrite system packages. This happens because Ubuntu already uses a package manager (APT) to control core Python packages. Ubuntu doesn’t want these packages changed directly, as it could break system tools that depend on Python.
That’s why modern Ubuntu shows the “external-managed-environment” warning.
In simple terms, it’s saying: “Don’t touch me , I'm managing this Python.”
Why it happens
This behavior is common in Linux and Unix systems, especially distributions like Debian or Ubuntu, which follow PEP‑668 to protect the system Python.
In practical terms:
System Python lives under : /usr/bin/python3
System packages live under : /usr/lib/... or /usr/local/lib/....
Pip is prevented from changing these system-managed packages unless you explicitly force it. That’s why the installer stops with an error instead of making changes silently.
Why this matters for malware analysis tools
Malware analysis tools often need specific or up-to-date library versions.
Common tools for offline VM-based research include Volatility 3, YARA, Capstone, pefile, radare2, binwalk, ssdeep, and Volatility plugins.
Installing some of these system-wide on Linux can trigger OS protections.
For a researcher, this is a problem: you need the tools to work, but you must not break the system or VM.
Solution for this blocker
Python virtual environments (venv) solve this problem. They create a safe, isolated workspace where you can install and run Python tools without affecting the main system. This lets you test, experiment, and use malware analysis tools freely.
What is a Python Virtual Environment?
A Python virtual environment is like a sandbox for Python. It creates a separate copy of the Python interpreter and a dedicated folder for all packages you install. Anything you install inside this environment stays there and removing that folder removes all installed packages and tools and gives zero impact on system Python.
This isolation is crucial for malware research because:
Malware testing often requires specific packages.
You don’t want system Python or other projects to break.
You can safely experiment without leaving traces on the main system.
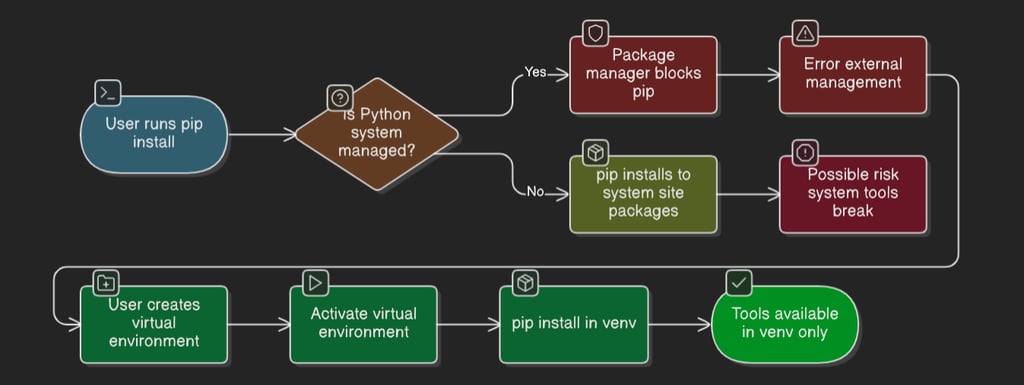
Steps to create virtual environment for analysis tools
Step 1: Intall venv (if not installed)
Run : sudo apt update
sudo apt install python3-venv python3-pip -y
Step 2: Creating the venv
Run : python3 -m venv ~/<foldername>
This gives you a separate Python environment so packages installed here don’t affect the system Python.
Step 3 : Activation
Run: source ~/<foldername>/bin/activate
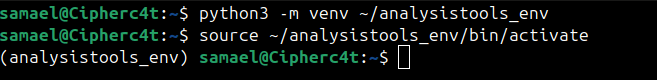
The PATH variable changes so the shell uses venv’s Python and pip. Your terminal prompt changes, e.g., (analysistools_env) user@vm:~$. Now any package you install goes inside this folder, not system Python.
Step 4: Installing packages for analysis tools
Example: pip install volatility3
Packages are installed inside ~/analysistools_env/lib/. Even if a package inside the environment breaks, the system Python and other projects remain safe. You can test the installed tools freely within this environment.
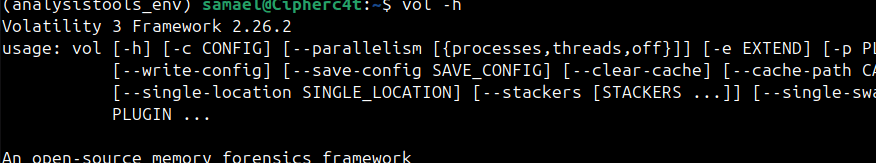
Step 5 : Deactivation
Run : deactivate
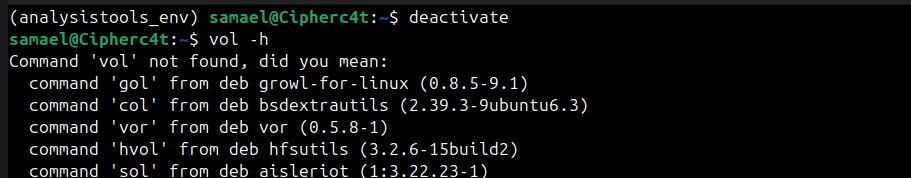
When you exit a virtual environment, the shell restores the PATH variable, returning to the system Python. This restores your environment to normal without affecting anything outside the venv.
Tools installed inside the environment won’t run outside it and will show an error, indicating that they are isolated.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.