How to Fix Kernel Verification Alerts in Linux
LINUX
Cipherc4t
9/30/20252 min read
With Secure Boot enabled on Linux, drivers like VirtualBox, VMware, or NVIDIA may fail to load.
These drivers need kernel modules, and Secure Boot only allows signed ones.
Unlike Windows, where Microsoft signs all drivers, Linux leaves signing up to distributions and users.
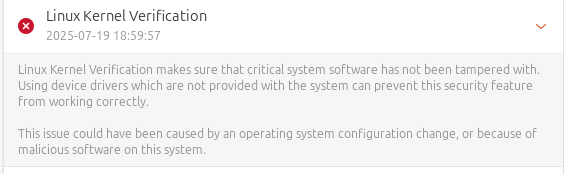
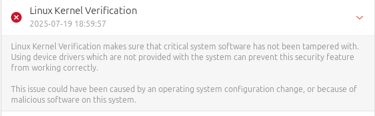
If the kernel is not properly verified, Linux security tools will flag it as:

Why this happens
In linux
Secure Boot checks the kernel and modules at boot to prevent rootkits.
Linux distributions sign the kernel, but third-party modules (VirtualBox, VMware, NVIDIA) are usually unsigned.
With Secure Boot enabled, unsigned modules are blocked.
Steps to Patch and Verify Your Linux Kernel
Step 1: Check Your Current Kernel
Run : uname -r
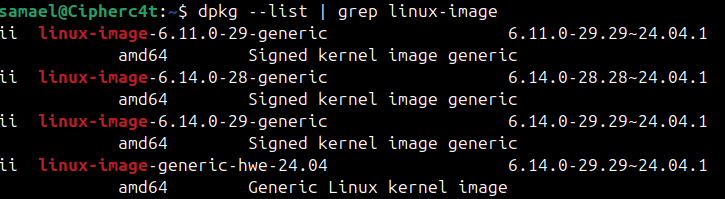
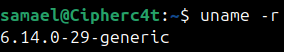
Here, the output shows:
The latest kernel should be marked as ii.
The signed kernel image indicates that these kernels are UEFI Secure Boot signed.
If Secure Boot is enabled in BIOS/UEFI, your Ubuntu system will only boot these signed kernels.
Step 5 : Reboot Into the New Kernel
Run : sudo reboot
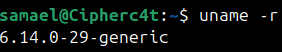
After the system restarts, verify the running kernel
Run : uname -r
It should now display the latest kernel version, indicating that the issue has been resolved by the Linux security tool
This displays the kernel version currently running on your system (for example, 6.14.0-29-generic).
Step 2: Update Package Index
Run : sudo apt update
Step 3: Upgrade Kernel and Related Packages
Run : sudo apt full-upgrade -y
This installs the latest generic kernel from the Ubuntu repositories and applies microcode and security patches.
Step 4: Verify the Installed Kernel
Run : dpkg --list | grep linux-image
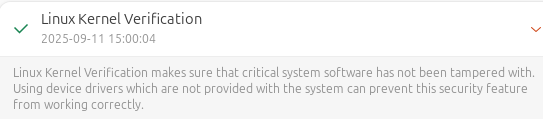
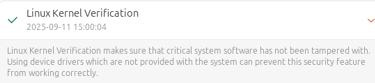
If the issue persists, check the Secure Boot status on your Linux system.
Step 6: Confirm Kernel Signing with Secure Boot Enabled
Run : mokutil --sb-state
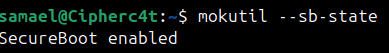
If it says SecureBoot enabled, your kernel is verified and signed.
If it says SecureBoot disabled, Secure Boot is off; you must enable it from the BIOS/UEFI.
Conclution
Secure Boot is often misunderstood. On Linux, it ensures that only signed kernels and modules can run at boot.
For malware analysis, if Secure Boot is enabled, VirtualBox or VMware may fail with errors because their kernel drivers are unsigned.
To run a VM on Linux with Secure Boot enabled without kernel signing issues, refer to this guide below.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.

