How to Fix the Intel GDS Mitigation Vulnerability on Linux (Ubuntu)
LINUX
Cipherc4t
10/2/20253 min read


What Is Intel GDS ?
GDS (Gathering Data Sampling) , also called the Downfall vulnerability, is a speculative execution side channel flaw found in certain intel CPUs (6th-11th Gen Core and early xenon). It allows malicious code to potentially leak data from CPU vector registers.
On Ubuntu , the security tool will flag this issue if your CPU microcode is outdated or the mitigation has not been applied. As shown in the below picture.
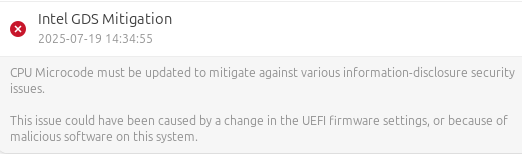
Steps to Fix Intel GDS Vulnerability in Ubuntu
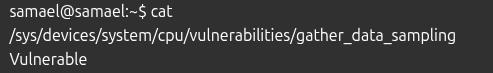
Step 1 : Check vulnerability status
Run: cat/sys/devices/system/cpu/vulnerabilities/gather_data_sampling
If it says vulnerable , you need to update.
Step 2 : Check is intel microcode is installed
Run : Apt-cache policy intel-microcode
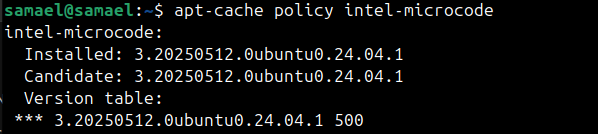
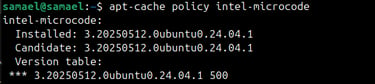
You should see an entry showing the installed version such as 3.20250512.0ubuntu0.24.04.1, or a newer release if one is available.
If Installed : none appears, it means the package isn't present.
Step 3 : Install or update intel microcode
Run : sudo apt update && sudo apt install intel-microcode
After installing , reboot the system so the updated microcode is applied at startup.
Step 4 : Verify mitigation
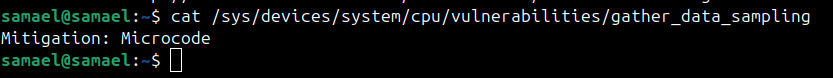
Run : cat/sys/devices/system/cpu/vulnerabilities/gather_data_sampling
It should show Mitigation : Microcode, indicating the vulnerability has been addressed.
What if the Mitigation Status Still Shows "Vulnerable"?
This indicates one of Two possibilities :
Your CPU does not have microcode mitigation for GDS (Common in many 6th-11th generation Intel CPUs) In this case, Intel has not issued a patch , so the kernel remains Vulnerable. We must wait for an official update.
Mitigation exists but is not enabled. Sometimes the kernel disables it by default to avoid performance impact . Here, mitigation can be forced by configuring the kernel through GRUB.
Steps to Enable Mitigation
Step 1 : Open the GRUB Configuration file
Run : sudo nano /etc/default/grub
Locate the line:
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash"
And change it to :
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash gather_data_sampling=force"
Save the file.
Step 2 : Update GRUB
Run : sudo update-grub
After updating , reboot the system and recheck the mitigation status as described in Step 4.
This forces GDS mitigation, and after verifying the system security, you should see that the issue has been resolved, as shown in the picture below.
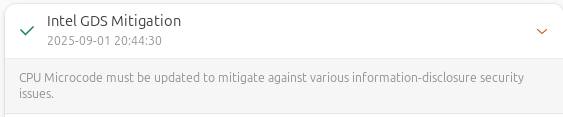
If it still shows “Vulnerable”
This indicates that Intel has not released a microcode update for your CPU model, so Ubuntu can only warn you—it cannot fix the issue. In this case:
Nothing is broken on your system; it’s an Intel design limitation without a patch.
If Secure Boot is enabled, the risk of exploitation is extremely low.
To maintain maximum safety, do not disable Secure Boot until an official update is released.
To run a full CPU vulnerability check on your Linux system, refer to the blog below.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.

