How to Check CPU Vulnerabilities on Linux and Apply Fixes
Check and fix CPU vulnerabilities on Linux to keep your system secure and running safely
LINUX
Cipherc4t
10/4/20253 min read


Modern CPUs, particularly Intel processors, have a history of hardware-level vulnerabilities such as Spectre, Meltdown, MDS, Downfall, and Retbleed.
These flaws reside in the CPU’s speculative execution and micro-architecture.
If left unpatched, malware on your system could potentially access sensitive data—like passwords, encryption keys, or browser information—from other processes.
For malware analysts and researchers, this risk is especially critical, as running malicious code in a lab environment can expose the host system through these CPU-level weaknesses.
Linux provides a built-in interface to check the CPU’s vulnerability status at runtime and exposes all available mitigations under :

Each file contains a plain-text status statement:
Not affected
Mitigation : <method>
Vulnerable
Steps to Perform a Complete Kernel Vulnerability Check on Linux
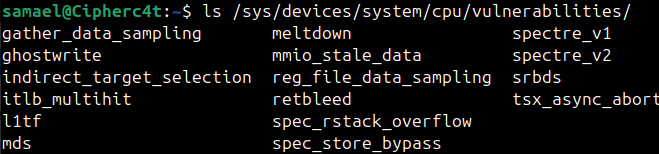
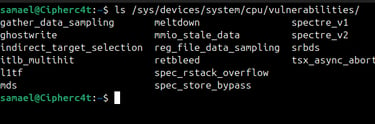
Step 1 : List all available CPU vulnerabilities.
Run : ls /sys/devices/system/cpu/vulnerabilities/
You should see files such as,
Step 2 : Read All Vulnerability Files
To read all files at once, run:
for f in /sys/devices/system/cpu/vulnerabilities/*; do
echo "$(basename $f): $(cat $f)"
done
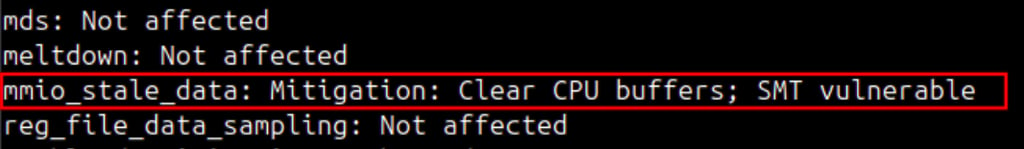
This command displays each CPU vulnerability along with the kernel’s current mitigation status.
Step 3 : Interpret the output
Mitigation: Your kernel and/or microcode has patched the vulnerability.
Not affected: Your CPU is not vulnerable.
Vulnerable: No mitigation is available for your CPU, or it has been disabled.
Note: For all vulnerabilities except mmio_stale_data (explained at the end of this section), the output should not show “Vulnerable.”
What to Do if the Other results Shows “Vulnerable”
Step 1: Ensure your system is fully updated.
Run : sudo apt update && sudo apt upgrade -y
Step 2 : Check and update the microcode package.
For Intel CPUs :
Run : sudo apt install intel-microcode
For AMD CPUs :
Run : sudo apt install amd64-microcode
If it still shows “Vulnerable,” it usually means:
Intel or AMD has not released a fix for your CPU (common in older generations).
Mitigation exists but is disabled by default due to performance impact. You can force it using a GRUB parameter. Refer to the Intel GDS mitigation blog to enable it manually.
Scope and Limitations of This Method
This method only checks CPU hardware vulnerabilities and their mitigations. It does not cover kernel bugs, application security issues, or network-level risks.
For Malware Analysis : Ubuntu applies the latest microcode updates and kernel mitigations by default. Checking manually ensures your hardware is safe and prevents malware in a VM from affecting the Linux host.
Some mitigations, such as mmio_stale_data, may still leave a small risk if Hyper-Threading (SMT) is enabled.
This is why here the status shows “Vulnerable”.
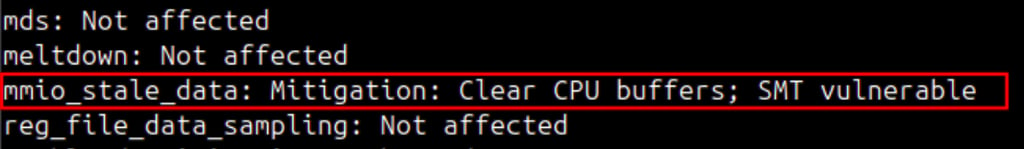
For maximum isolation, you can disable SMT in the BIOS.
This will mitigate the vulnerability, though it may reduce performance.
To learn more about the mmio_stale_data vulnerability, refer to this blog below.
All rights reserved © 2025 - Present MalwareHunts. For educational and research purposes only. MalwareHunts is not responsible for any misuse of the information provided.